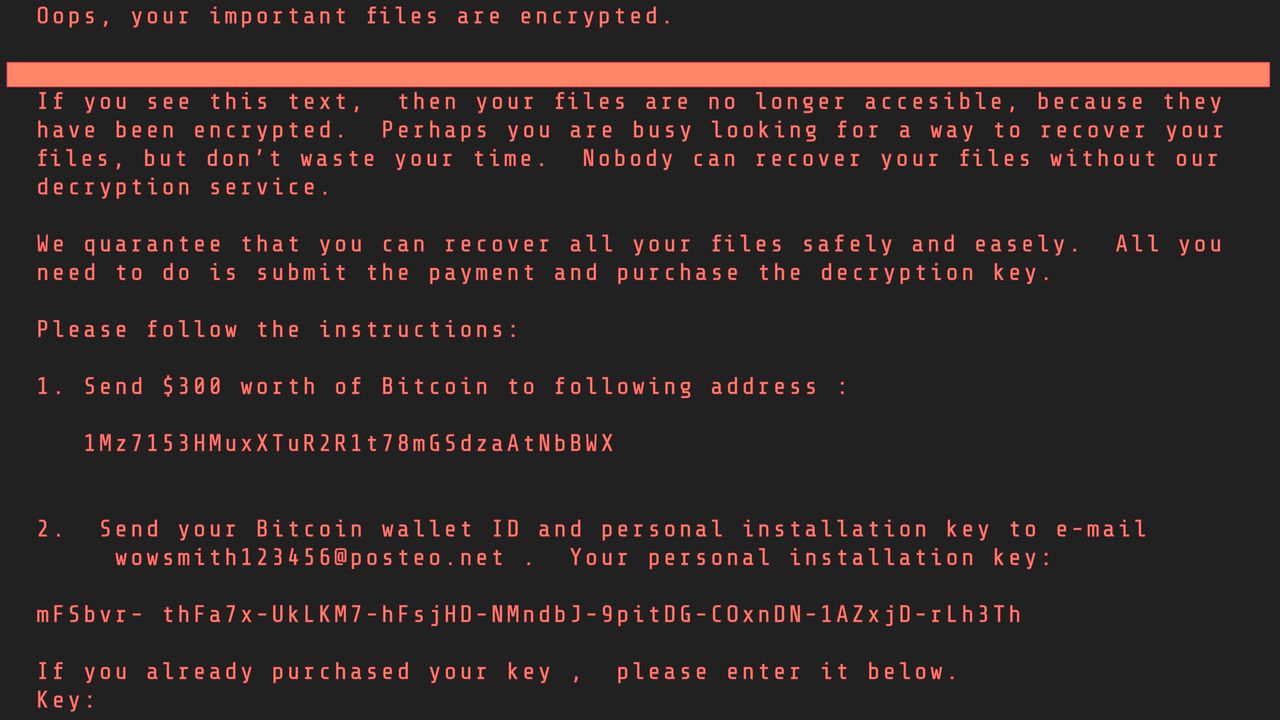
Petya – this is the virus that caused the biggest hacker attack in the history of independent Ukraine.. It targeted banks, national authorities and important companies. Despite the fact that the virus also attacked computers in other countries, Ukraine suffered over 75% of all infected computers. It is certain that despite its similarity to WannaCry, the aim of Petya was not to encrypt computers in order to obtain a ransom. The Ukraine Security Authorities announced on Saturday, that Russian Secret Service were responsible for the attack with Petya virus.
The attack started on 27th June at approximately 11:30 a.m. Computers running on Windows OS, which most likely did not include the latest security updates were affected by the virus.
Petya also hit national authorities and private companies. First, information on attacking Ukraine banks was published. Seven large banks suffered but the biggest commercial PrivatBank was not affected, or at least they did not notify this issue. Soon, it turned out that the problems also affected national structures such as the network and websites of some government institutions, police, Lvov authorities, etc. Important facilities of communication infrastructure also turned out to be a target: Boryspil International Airport in Kiev, underground in Kiev, Ukrainian railways and a number of large private companies, including the power company, three mobile operators, media – including TV stations and others. A system for radiation control was activated in the former Nuclear Power Plant in Chernobyl.
The first version of Petya was recorded in March 2016. Similarly to WannaCry, Petya caused encryption of computer drives. After a restart, a message with the request of ransom was displayed for the bitcoin equivalent of USD 300. Nevertheless, according to experts this was just a cover-up. The virus did not aim at extorting money from owners of infected computers but it caused a paralysis of devices and destroyed data stored on hard drives.
Experts state that Petya was distributed through the mechanisms of updates in the M.E.Doc accounting software that is used by numerous institutions and companies working on government documents.
Such a version is confirmed by SBU, also indicating that “the key task of the virus was to destroy important data and create obstacles in the work of national authorities and private companies in Ukraine to cause panic among the society.” It is hard to say whether it is justified to state “cause panic” but the version confirming destabilisation of the situation in Ukraine through paralysis of institutions seems to have grounds.
SBU refers to consultations with experts from international companies in charge of network security, which state that the last attack was executed by the same hacker groups as those that attacked Ukrainian financial and power institutions in December 2016. This indicated Russian origin of the virus.
Luckily, Petya did not turn out to significantly affect private citizens. The difficulties that were faced by Ukrainians include blocking some bank payment terminals. In Ukraine, it is popular to make payments for various services via terminals, not through the internet. The virus also caused disruption in the work of Nova Poshta – the biggest courier company as well as Rozetka, the biggest online shop.
The key question is: what was the real target of the attack and who is behind it?
There is no clear answer. Some experts say that the main target of the virus is Ukraine’s infrastructure. In other countries the virus was not so much distributed as compared to Ukraine and it was not as harmful. It is possible that this was an effort of inspecting how susceptible Ukrainian infrastructure is to cyberattacks. It is worth reminding one that there is a war currently in effect in the east of Ukraine which experts call a “hybrid war”. At this point there is no evidence that Russia is responsible for the Petya attack. Also in Russia there were some news that the virus attacked a number of local banks and companies including Rosnafta. Nevertheless, this could have only been a “ricochet” of the attack in Ukraine.
In the West, there have been comments that NATO’s interest includes helping Ukraine in creating a proper security system. It is worth mentioning that after the attack in 2007 on Estonia, the Cooperative Cyber Defence Centre of Excellence was created. However Ukraine is neither a member of NATO nor EU.